The transition to remote working and dramatic changes to business practices during the COVID-19 pandemic has corresponded with an increased threat of malicious phishing campaigns, as attackers leverage this ‘new normal’. As a feature of our regular security monitoring activities, including a focus on domain safety, Kinetic IT continues to identify newly registered domains of interest that could be used for malicious purposes. These domains may contain threats to Australian workers, based on use in spearphishing campaigns. Kinetic IT’s Will Smith looks at domain safety and investigates a real-life example of a suspicious domain.
A potential threat
We recently investigated this domain and flagged it as potentially suspicious: com.au.finddeals.info
Based on the name alone, it’s difficult to confirm how risky it might be. Without more investigation, it’s impossible to tell if it’s intended for spearphishing or is a legitimate site for customers to access the latest Australia Post Online Catalogue offers.
How to gain more insight into potential threats
Unfortunately, Google won’t – or didn’t at the time of writing – categorise these domains as malicious, likely due to how recently they were registered. Nevertheless, there are open-source and freely available tools we can use to gain more insight into potential threats, and manage domain safety, without having to interact directly with malicious infrastructure.
One popular service owned by Google is VirusTotal. Initially created as a central repository to test and collate malware samples, VirusTotal’s capabilities have grown beyond being a simple AV aggregator. Even VirusTotal’s entry-tier Community Account provides metadata on the relationships between malware, hosted infrastructure, and associated URLs. This metadata helps investigators determine if domains contain threats (irrespective of whether they are legitimate, infected domains, or domains specifically set up by scammers).
RELATED CONTENT: Common cyber security mistakes and 3 simple ways to fix them
Using VirusTotal
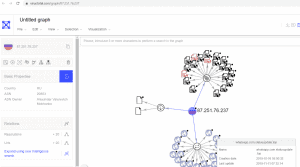
Back to our example. By entering the newly observed domain into VirusTotal, it reveals more information about possible threats. Firstly, the server IP address appears to be associated with several suspiciously-named domains, represented in the figure below as little blue world icons. Manually highlighting these icons will bring up the exact domain values, with whatsapp.com.statusupdate.top a specific example:
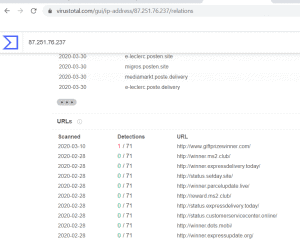
Diving deeper again, URLs attached to the same IP can be a regular occurrence, but it’s when names or values look suspicious that it should raise the red flag:
Based on a quick review, the domains exhibit tell-tale signs of being part of a spam distribution network – similar to those used to entice victims via SMS text messages to collect the iPad they never ordered.
RELATED CONTENT: COVID-19: Is it business as usual for cyber security?
What next in domain safety?
Does this mean that we could safely ignore these domains? The simple review we’ve just conducted suggests the site is mostly innocuous and could be safely ignored from an enterprise perspective. But that doesn’t mean things won’t change. Like we’ve adjusted our lifestyles to meet the COVID-19 challenges, so too will attackers. Their industry requires continual evolution and innovation to stay ahead of security defences, so they are adept at adjusting their tactics.
Occasionally, spammers reuse infrastructure to make their lives easier, so keeping track of innocent-looking historical data can prove fruitful when investigating more advanced threats. Remember, today’s spammers breed tomorrow’s spearphishers, so stay alert to domain safety and keep a watchful eye on malicious domains. It could save your business.
You can find more insights about domain safety and best cyber security practices on our website.