OT Security is becoming an ever more critical concern as recent cyber attacks demonstrate the far-reaching consequences for both digital and physical systems.
The Hezbollah supply chain attack in Lebanon, where radio systems were intercepted and weaponised to cause mass casualties, serves as a stark reminder that threats to operational technology (OT) can have devastating real-world consequences, far beyond the digital realm.
As Australia’s digital footprint continues to expand, the risk of OT security systems being targeted grows ever more acute. The 2023 Cyber Threat Report from the Australian Signals Directorate (ASD) paints a sobering picture: both state and non-state cyber actors are persistently probing Australia’s critical infrastructure, driven by the intent to disrupt, compromise, or exfiltrate valuable data.
The attack on Hezbollah’s radio supply chain underscores the risks associated with cyberattacks on non-traditional information technology (IT) systems. In this case, intercepted communication devices were used to orchestrate an assault that resulted in significant physical harm. This incident demonstrates how attacks targeting OT, which controls physical processes, can have far greater implications than traditional cyber incidents like data theft or service outages.
In the Australian context, such attacks would pose severe risks to public safety, national security, and economic stability, making OT security an issue of critical national importance.
Why OT Security Matters
While IT security has been honed over decades, OT systems often lag behind in terms of protection. Historically, OT environments—such as those managing water treatment plants, electricity grids, and transport networks—were considered isolated and less susceptible to external threats. But the rapid interconnectivity of OT and IT systems has revolutionised industries, creating efficiencies that also introduce new vulnerabilities.
As critical infrastructure operators adopt these interconnected systems, cyber actors now have opportunities to manipulate physical processes, disrupt services, or cause direct physical damage. In a country like Australia, where essential services span vast areas and rely heavily on OT, the stakes are high. A breach in the industrial control systems (ICS) underpinning these services could result in catastrophic outcomes—ranging from economic upheaval to loss of life.
The Growing Threat to Critical Infrastructure
Australia’s critical infrastructure is increasingly under siege. The 2022–2023 ASD Cyber Threat Report highlighted a notable rise in cyber incidents, with OT and ICS environments becoming prime targets. Malicious actors, from ransomware groups to state-sponsored entities, are exploiting vulnerabilities in OT systems, aiming to disrupt operations or gain access to sensitive data.
In some cases, state actors use these attacks to pre-position themselves within networks for future operations, allowing them to remain undetected for extended periods, ready to strike when the time is right. One alarming trend is how cybercriminals exploit unpatched OT systems.
As corporate IT and ICS networks converge, adversaries are using this interconnectivity to breach OT environments through traditional IT routes. The result? A wider attack surface, making ICS systems more susceptible to attacks that can halt operations, cause severe economic damage, and, in the worst cases, endanger lives.
Australia’s National Security at Risk
The risks posed by OT vulnerabilities extend beyond corporate and economic losses. These systems represent a cornerstone of Australia’s national security. As the ASD report stresses, foreign adversaries—especially state-sponsored actors—have increasingly set their sights on ICS environments, not only for espionage but also as part of long-term strategic operations designed to cripple Australia’s resilience in times of crisis.
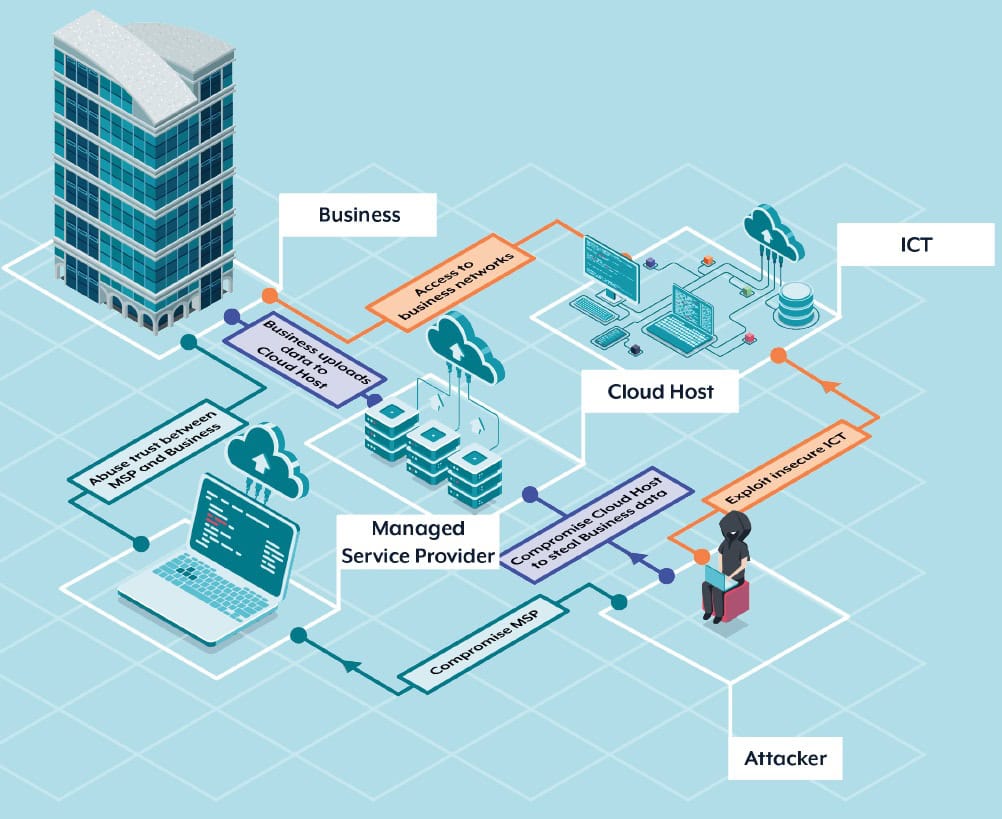
Figure 6: ICT Supply Chain Threats (Source: ASD Cyber Threat Report 2022-2023)
For instance, a successful attack on the power grid or transport system could have a cascading effect, paralysing essential services and impeding Australia’s ability to respond to national emergencies. The potential for extended outages in key sectors such as energy, healthcare, and telecommunications presents a grave risk to public safety and economic stability. Additionally, prolonged disruptions could weaken Australia’s defence capabilities, exposing the country to broader threats in times of geopolitical tension.
The Need for ICS-Focused Cybersecurity
Addressing the vulnerabilities in OT systems requires a bespoke approach that goes beyond traditional IT security measures. ICS environments have unique requirements—uptime and operational continuity often take precedence over routine patching, and the latency-sensitive nature of OT means that standard cybersecurity practices may not always be applicable.
For Australia’s OT environments, a mix of advanced technology and expert human oversight is crucial. This is where partnerships with specialised OT security providers play a critical role. Take, for example, the collaboration between Kinetic IT and Dragos, a global leader in OT security. While Dragos brings cutting-edge threat detection capabilities tailored specifically for ICS environments, Kinetic IT delivers hands-on expertise in managing and defending these systems in real-time. Such partnerships are instrumental in protecting Australia’s critical infrastructure from evolving cyber threats.
RELATED: The Pragmatic Essential 8 Approach Every Government Organisation Should Know
Collaboration is Key
Ensuring the resilience of Australia’s critical infrastructure demands a coordinated effort from all stakeholders—government, private industry, and security providers. The ASD has repeatedly called for closer collaboration between these sectors, recognising that a robust cybersecurity posture relies on shared insights, advanced threat intelligence, and real-time response capabilities.
To that end, Australia has made significant strides in building a national cyber resilience framework. The ASD’s Cyber Threat Intelligence Sharing (CTIS) platform is one example of how collaboration can help detect and neutralise threats before they cause harm. By pooling information from government agencies and industry partners, CTIS enables stakeholders to share vital threat data, empowering them to better defend their networks against malicious actors.
As ICS environments become more integrated with IT networks, the risks to Australia’s critical infrastructure will continue to grow. Protecting these systems from sophisticated cyber threats is no longer just a cybersecurity issue—it is a national security imperative. By investing in ICS-specific security technologies and fostering partnerships that combine technical expertise with advanced threat detection capabilities, Australia can bolster its defences against the growing threat landscape.
By Tony Campbell, Principal, Security Consulting & Advisory, Kinetic IT
















